Muti-Factor Authentication is a necessity. We aren’t arguing against that. Quite the opposite. We highly recommend it.
Today, we want to outline how malicious actors can bypass your MFA controls using relatively simple techniques.
Some of these techniques can compromise your employees without anyone ever knowing.
So, Is MFA enough? Let’s dive deeper.
Contents
What is Multi-Factor Authentication (MFA)?
Muti-Factor Authentication, or MFA, is an additional security layer that helps protect applications against unauthorized access.
MFA can come in several flavors: texts, push notifications via apps, or even physical security keys.
Traditionally, logging into an application requires a username and password, otherwise known as credentials.
Malware or social engineering techniques will often look for and steal these credentials. MFA is an additional check after entering in credentials to prove you are who you say you are.
So:
If a malicious actor has stolen your credentials, they will face an additional security check preventing them from finishing the authentication.
This is how MFA helps provide an additional layer of security.
Is MFA Enough?
What if I told you that, according to Verizon’s 2022 DBIR, nearly half of all cyber attacks start with employee stolen credentials?

But how can this be true if MFA is in place? Shouldn’t MFA prevent them from logging in if they have to provide an MFA code?
Good question.
If you view your organization’s security posture, it’s more than just a straightforward application. It’s layers and layers of different applications and infrastructure. And most of these layers use web authentication services to manage them. Therefore, they are vulnerable to credential theft.
Many of these authentication service MFA protections are by-passable.
We’ll explain how threat actors hi-jack session tokens via credential stealer malware.
Credential Stealer Malware
In the past, we were told we needed to look out for phishing emails because that’s how malicious actors get to us and ultimately steal our credentials..
But malware stealers take this a step further.
Often, we use Google to search for free third-party software or other random tools. You’ll notice sometimes the top several search results are sponsored links.
We might look for cheats for video games or free Adobe Photoshop. Other times, we’re looking for free Microsoft Office or online books in PDF format.
Threat actors know precisely what we are looking for, and all they do is create Google ads for these programs. When you search for these programs, the top result will link to the threat actors’ software that appears benign.
From these websites, you’ll unknowingly install malware. The malware is not persistent. In other words, it will execute, harvest everything it needs, and then uninstall itself, leaving no traces.
Pretty scary.
When a computer is infected, it’s not just one password to the computer or a single email. The stealer extracts your entire browser settings. This can include credentials saved in the browser.
It also steals cookies which contain authorization and session tokens.

From there, the threat actors will use dark web marketplaces to sell the stolen information, including:
- Fingerprints (fp)
- Cookies
- Inject scripts info
- Form grabbers
- Saved logins
- Other personal data
Session Tokens in Cookies to Bypass MFA
Using the credential stealer malware, criminals harvest session tokens from your cookies. Or, a malicious actor purchases cookies on the Genesis Marketplace.
These cookies contain session tokens. Session tokens identify established connections between a client and an application. These prevent users from re-entering their credentials every few minutes because session tokens have a set expiration date.
Marketplaces For Session Tokens
In the case of the Genesis store, they went even further. They created Genesis Security.
Genesis Security is a plugin for your browser. It helps criminals to seamlessly buy stolen credentials with one click and import them to impersonate your employees. The plugin will also grab fingerprints harvested from your computer.
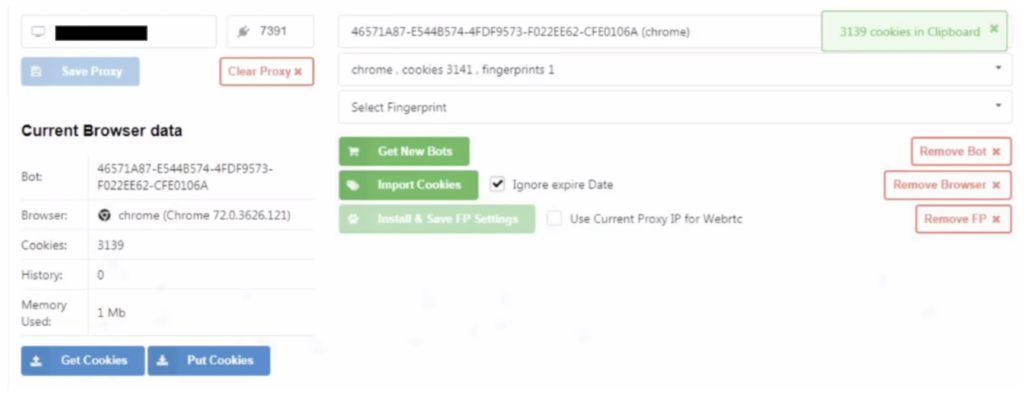
This means the criminals can impersonate and log in as your employees even if MFA is in place. This is because Chrome sometimes stores the session tokens already authorized by MFA.
How Long Do Cookies Last?
Some cookies expire instantly, others decades later. It always depends on the admin who configured the service.
Take a look for yourself. Go to Google Chrome’s developer tools to view how many cookies Chrome stores.
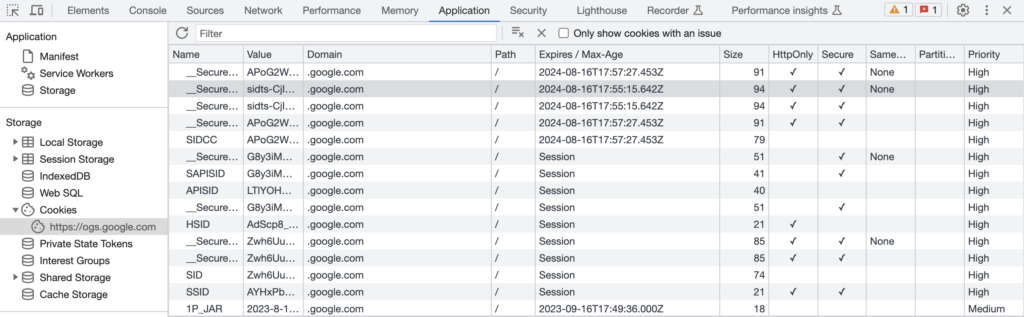
Looking above, you can see some cookies expiring a year from now. Ultimately, the answer will vary. Just keep in mind that cookies enhance user experience. They prevent websites or applications from constantly requiring you to log in.
Keeping this in mind, there will be configuration mistakes from administrators who issue the tokens.
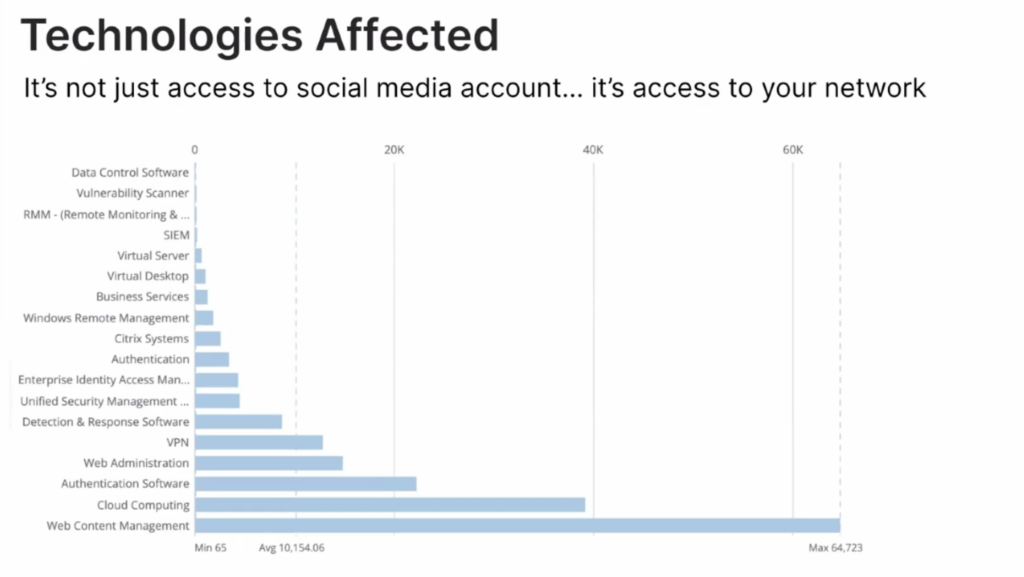
Technologies Affected by MFA By-Pass
According to Recorded Future, it’s not just social media logins that session tokens contain. There are plenty of risky credentials to access your network, like VPN access, Virtual Desktop management, and Cloud Computing access.
Bolster your Security with Threat Intelligence
This leads us to the question. What do we do then?
Many Threat Intelligence providers have access to the dark web marketplaces. They will insert themselves between buyers and sellers and notify clients of credentials and session tokens for sale.
Visit our Threat Intelligence guide to get started.