If we were to guess, you’ve heard a lot of talk about automation. Your CISO or manager wants everything automated, especially repetitive incident response tasks like investigating phishing submissions or dynamic blocking.
Without a doubt, some of the newest and most exciting technologies to enter the cyber enterprise are Security Automation, Orchestration, and Response tools.
Regardless of your professional cyber security experience, you will find takeaways from this article. Welcome to our SOAR tool guide.
Contents
What is a SOAR Tool?
Security Automation, Orchestration, and Response (SOAR) solves several challenges: case management, automating incident response, and threat intelligence management.
A standard SOAR tool has hundreds of API integrations with other cyber security and software vendors that allow you to automate those tools. Combining these integrations allows cyber security engineers to build ‘playbooks’ to automate incident response with actions like containing endpoints, blocking indicators of compromise, or even resetting employee passwords.
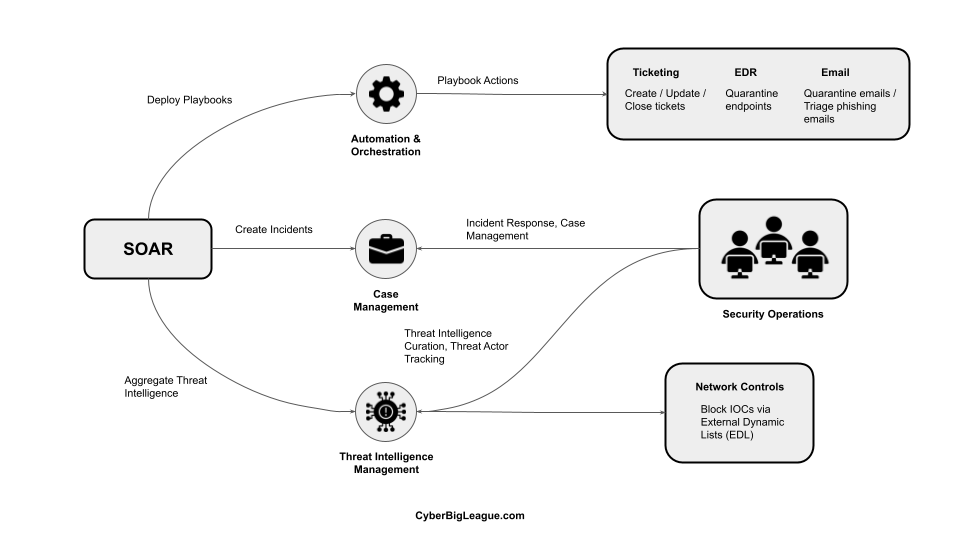
The leading cyber security enterprise tools that integrate into SOAR are endpoint detection and response (EDR), security information and event management (SIEM), and firewalls. However, software like Microsoft Exchange, Slack, and ServiceNow can also easily connect and integrate.
These automated actions can now be built in-house with a scripting language like Python, but enterprise-grade SOAR tools include reusable and pre-built actions. These pre-built actions form playbooks and communicate with other vendor tools with API requests.
In conclusion, a SOAR tool and its components form a case management system, allowing engineers to build playbooks to automatically respond to cybersecurity incidents.
Playbooks
Playbooks and their actions run on cases or incidents within the SOAR tool. Cases and incidents – depending on what the vendor names them – are treated as objects. These objects contain relevant information, such as IOCs and events generated from a different tool like your EDR but are most commonly forwarded from SIEMs.
Put another way, cases contain all the information relating to the original incident. An example could be an account lockout alert, the relevant information being the username, source IP address, and source hostname.
What is the Difference Between a SOAR Tool and SIEM?
The only similarity between a SIEM and a SOAR tool is incident management. Both tools help security teams manage and respond to alerts. The main differences are below:
Collecting and Aggregating Logs
SIEM tools collect and aggregate log and security event data centrally from various security tools, servers, databases, and applications. Cyber security engineers build correlation rules using this data to alert on malicious activity. These SIEM-generated alerts require constant manual tuning and response.
On the other hand, a SOAR tool doesn’t collect or aggregate log data. It lets the SIEM handle this. Instead, the SIEM forwards its alerts to the SOAR tool for automation.
Built-in Automation

In short, a SIEM doesn’t have built-in playbooks that can automate tasks. For the most part, the closest a SIEM gets to automation are reusable saved search queries. On the other hand, a typical SOAR tool includes hundreds of pre-built customizable actions and playbooks.
SOAR Use Cases
Phishing Response
It’s common practice to have employees report suspected phishing emails. If we were to guess, it’s likely people aren’t jumping up and offering to review these emails. In fact, it is an often overlooked manual and tedious process – however, that isn’t to say reviewing reported phishing emails isn’t essential.
Typically, reported emails arrive in a designated inbox for manual review. This tends to be a repetitive task of inspecting URLs, the sender’s domain, and other indicators. An analyst will manually search and delete similar emails after examining indicators and determining if the email is malicious.
This is where a phishing playbook helps. SOAR tools like Splunk SOAR and XSOAR can monitor and poll email inboxes. Every time SOAR polls an email, it ingests and creates an incident for it. The best part is tools like Phantom and XSOAR will parse all domains, URLs, and IP addresses from the email for you. Before any significant automation has been done, you are already saving a lot of time.
Next, threat intelligence and reputation tools like Recorded Future or VirusTotal enrich the IOCs. If an IOC has a malicious or suspicious risk, you can be confident it was a phishing attempt.
To finish off, simply run a search on emails throughout your Exchange server to find similar emails from the same sender. For each email, either delete it or move it to a designated inbox for further review.
To summarize a phishing response playbook:
- Configure SOAR to monitor and poll a phishing inbox
- Configure SOAR to ingest and create an incident for each email
- Extract IOCs from phishing emails and add them to the incident
- Build a playbook to run each IOC through an enrichment lookup
- Identify sender email addresses for IOCs that return as malicious
- Search Exchange for emails from the sender
- Delete or move any found emails
Dynamic Blocking
Most SOAR tools can host external dynamic lists (EDL) via HTTP. A typical EDL contains single-column entries of IP addresses or URLs. The popular method is to host three lists on your SOAR: URL, Domain, and IP lists. You can configure firewall policies to read and ingest entries on the EDL for blocking purposes. The firewall will constantly poll the lists to reflect changes.
Moreover, once you have created a list, you can build a playbook to automatically add new IOCs from incidents. Think about when you manually identified malicious IOCs in incidents and added them to a block list. A playbook can do this for you.
Ultimately, dynamic blocking works well with the phishing use case. After all, the phishing email IOCs are already extracted. Engineers can spend time tuning and building additional correlation rules by automating blocking IOCs.
Additional SOAR Use Cases
In conclusion, there are dozens of SOAR use cases besides dynamic blocking and phishing; however, dynamic blocking and phishing should get you started. Here are several more ideas for SOAR automation:
- Creating tickets
- Resetting compromised account credentials
- Vulnerability management scans
- Malware analysis and sandboxing
- Indicator hunting
For advanced Security Operation teams, read our guide on configuring Automated Threat Hunting between your SOAR and SIEM.
