Undoubtedly, Splunk is a leading competitor in the cyber security space. Compared to other security information and event management systems (SIEM), we collaborate with it the most in our field and notice customers talk highly of it. Splunk becomes a true SIEM when it’s enhanced with Enterprise Security.
Now:
Let me guess. You are here because you are tired of your old SIEM and want to upgrade. Or you have taken up a new job role and have been handed a Splunk SIEM tool to work out of.
Regardless of the two, you will find valuable takeaways from here.
Contents
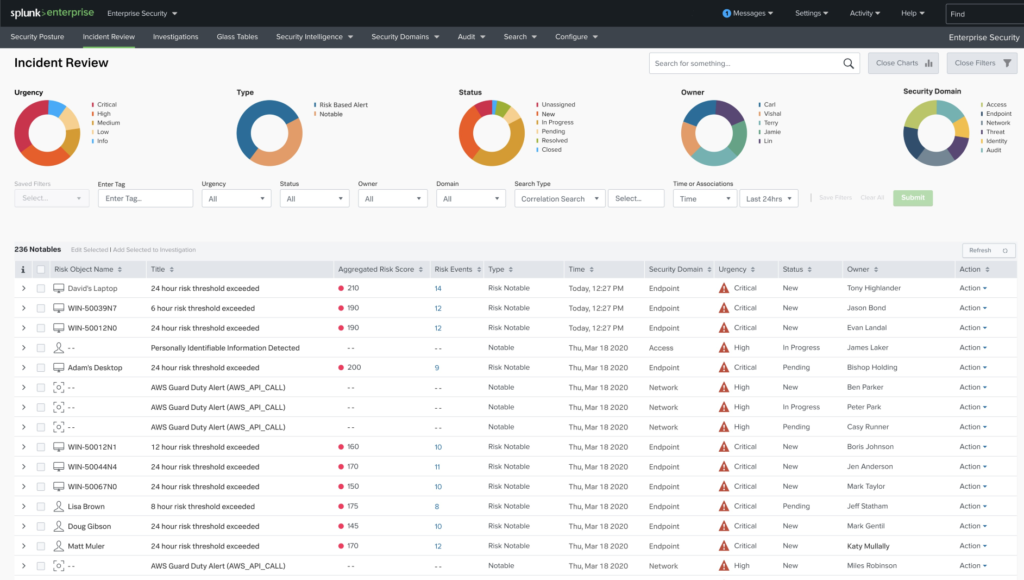
What are the Concepts of Splunk?
Cyber security professionals use Splunk, a popular log management tool, to address the challenge of responding to many alerts and logs.
It is a SIEM that analysts use to analyze and visualize large amounts of data. Cyber security engineers build correlation rules on top of the data to trigger real-time notable events. The real power of Splunk is to ingest any human-readable data.
Before going too deep into Splunk, it is worth explaining general concepts.
Splunk Enterprise:
It is the basic form of the tool that can come in two flavors: On-premise or cloud. Technically, it is a data analytics platform that makes sense of copious amounts of data.
In short, Splunk Enterprise is a software, whereas Splunk Enterprise Security is an application on top of it, which turns it into a true SIEM.
Companies utilize the base enterprise flavor to function as an SIEM, but most have the Enterprise Security add-on.
It comes with the ability to:
- Aggregate and query logs
- Build correlation rules for monitoring and alerting.
- Generate reporting and metrics
- Incorporate machine learning
Splunk Enterprise Security:
Enterprise Security comes with all the base Enterprise features, but it is when Splunk becomes a SIEM. It can do everything Enterprise can but more, including the following frameworks:
- Asset and Identity Correlation
- Notable Events
- Threat Intelligence
- Risk Analysis
- Adaptive Response
Collection of Frameworks
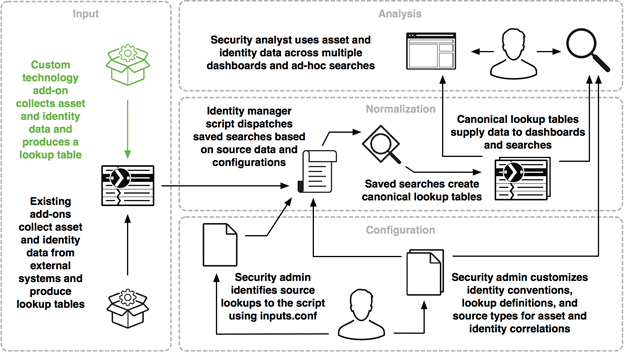
Asset and Identity Correlation
Sometimes, events have fields or properties that include information relevant to identifying an asset or user. To name a couple, these fields could be an IP, DNS, or MAC address or a LDAP username.
Engineers can create custom data collection add-ons to extract and prepare this data for ingestion by Splunk ES, and dispatch saved searches to create lookup tables. Analysts can use these saved searches, lookup tables, and dashboards to identify assets and users within their networks.
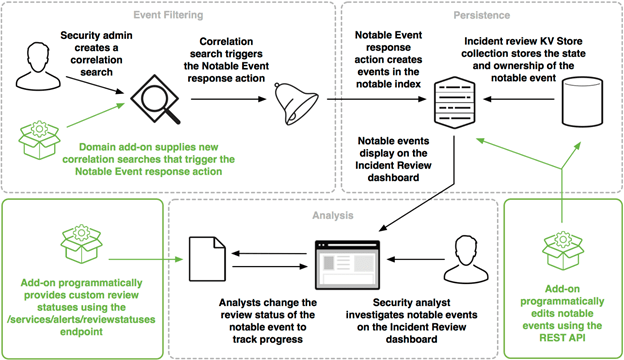
Notable Events
An engineer can build notable events only available in Enterprise Security to manage better the ownership, triage process, and the state of incidents. Most notable events trigger automatically via correlation searches, but engineers can also create them manually.
An example could be correlating outbound traffic against confirmed C2 servers supplied by threat intelligence. When the correlation finds a match, trigger a notable event.
This framework allows analysts to triage and prioritize those triggered events.
Threat Intelligence
The Threat Intelligence framework does what the name implies: consuming and managing threat feeds. With this, an engineer can correlate existing data with threat intelligence to create notable events on matching activity. The framework supports a large amount of threat intelligence types. The types correspond to the KV store collections where the threat intel resides:
- X509 Certificates
- File names
- Hashes
- URLs
- IP addresses
- Domains
- Processes
- Services
- Users
- Registry entries
Risk Analysis
The Risk Analysis framework goes hand in hand with the Identity framework. Using the gathered identities, an Engineer can build risk modeling on their activity based on expected behavior.
Splunk ES has built-in correlation searches for risk analysis and correlating machine data with asset and identity data. Correlation searches search for a conditional match to a question. When a match is found, an alert is generated as a notable event, a risk modifier, or both.
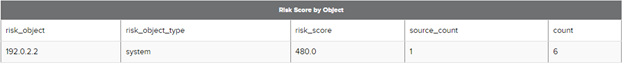
Events that modify risk are called risk modifiers. These live in the risk index, which contains:
- Score
- Object
- Object Type
- Description
A risk score is a single metric that shows the relative risk of a device or user over time, whereas a risk object represents a system, a user, or an unspecified other.
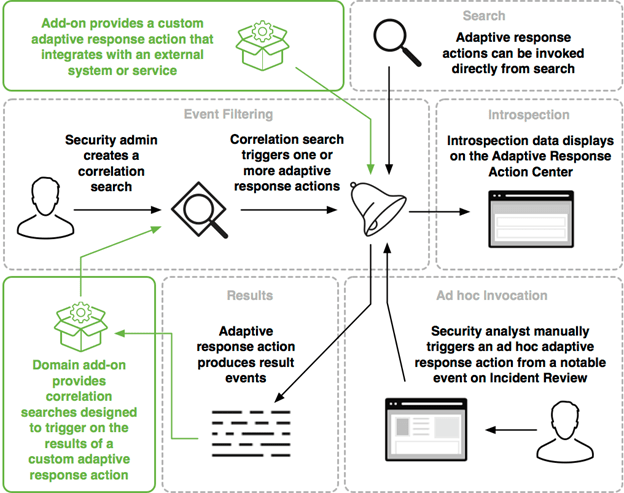
Adaptive Response
Our favorite piece of Splunk is this one. Adaptive Response allows pre-configured actions to trigger by correlation searches automatically. A splendid example often used by mature teams is to create ServiceNow tickets via adaptive response actions automatically.
The unique part is the technology add-ons. Enterprise Security can integrate with various technologies like vulnerability management, ticketing systems, or endpoint agents.
There are two ways to invoke response actions:
- Match the trigger conditions of a correlation search.
- Manually running the action.
The Architecture of Splunk SIEM
Splunk is a SIEM, not an IDS. It needs to accomplish two things: indexing and searching.
Think about it. You are throwing terabytes of data, all structured in unique ways. Splunk needs to make sense of this data so that you can query and search it. This is where indexing takes place and is where Splunk strives compared to its competitors.
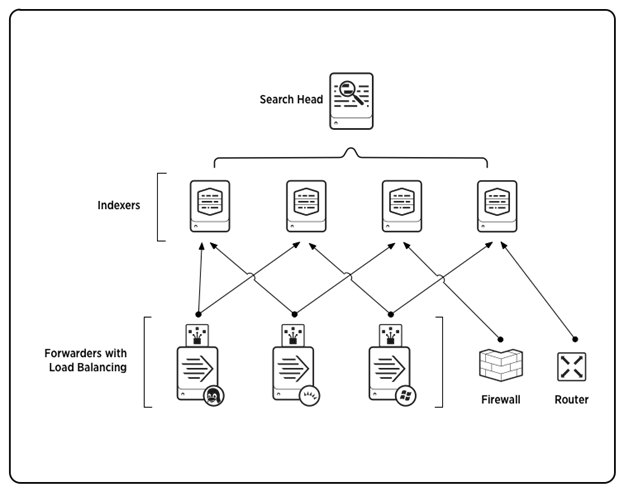
Indexer
The indexer transforms raw data into events, thus placing the results into an index. It can also search already indexed data in response to search requests.
Search Head
So. What happens when you have multiple indexes? Good question. Use a search head.
In a distributed search environment, the search head’s main objective is to direct searches to the correct index and to merge results back to the user who performed the search.
Forwarder
Sometimes, data must be shared between or sent from one index to another. There are three types:
Universal forwarder: a dedicated version that contains only the essential components needed to send data. This is the best way to forward data to indexers in most situations. Its main limitation is that it delivers only unparsed data.
Heavy forwarder: has a smaller footprint than a Splunk Enterprise indexer but retains most of the capabilities. Its exception is it cannot perform distributed searches. Unlike other forwarder types, a heavy forwarder parses data before forwarding it and can route data based on criteria such as source or type of event. You must use this type of forwarder to route data based on event contents.
Light forwarder: has most features disabled and has been depreciated as of Splunk Enterprise version 6.0.0. It has the most negligible impact on system resources.
Deployment Server
Lastly, a Splunk instance can serve as a deployment server. This tool distributes configurations, apps, and content updates to groups of instances. You can use it to distribute updates to most Splunk components: forwarders, indexers, and non-clustered search heads.
How Does Splunk SIEM Compare to other SIEMs?

Benefits of Splunk SIEM
When it comes to the benefits, Splunk SIEM has four core standouts:
Scaling: Out of all its competitors, Splunk scales the most effectively. It happens to be the reason Splunk gained incredible popularity in the first place. Scaling is significant whether on-premise, cloud, or hybrid. Besides the costs, you don’t need to worry about log retention and adding additional log sources.
Flexible search and reporting: You can customize just about anything in Splunk. All the dashboards and graphs are powered by the same search method using Splunk Querying Language (SPL). The underlying data can be manipulated and presented exactly how you want it to look. If you’re tired of fixed built-in dashboards and graphs that you can’t change, this is the tool for you. This is the main reason Splunk is the best SIEM.
Ability to index any data type: This is one of Splunk’s most significant bragging points. It is a machine-learning platform that can ingest any human-readable, non-binary data. You can even connect to databases to collect access and behavior logs.
Technology add-ons: Just about every big cyber security vendor integrates with Splunk. When choosing a SIEM, you want to ensure it can integrate with your existing toolsets.
Limitations of Splunk SIEM
For the most part, Splunk is our SIEM of choice. With any perfect tool, though, there are limitations. We find those to be:
Tough to learn: To get value out of Splunk SIEM, you will need at least two full-time dedicated engineers building out correlation searches and notable events. It can take years to master SPL truly.
Costs: It isn’t cheap. Splunk has the business model of charging based on the data you are bringing in. As you bring in logs, you will want to continuously add more once you realize how awesome it is to search from a single pane of glass.
Heavy on resources: Although it scales excellent, be prepared to constantly upgrade the specs you’ve installed Splunk SIEM on to support its capabilities.
